注意:部分文章发布时间较长,可能存在未知因素,购买时建议在本站搜索商家名称,先充分了解商家动态。
交流:唯一投稿邮箱:hostvps@88.com。
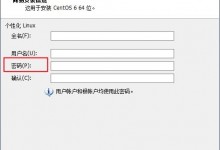
自从安装了DA面板后,Brute Force Attack暴力破解DA后台密码就没有停止过,或许见多了就不怪了,但是老是收到诸如此类的信息:Brute-Force Attack detected in service log from IP(s) 106.187.43.249,总不是一件让人很愉快的事儿。directadmin官方有教程,如何屏蔽ip阻止Brute ForceAttackhttp://help.directadmin.com/item.php?id=380以下我将官方的教程汉化下:1)第一步,配置iptables,让block_ip.sh生效,DA官方的iptables文件适用于CentOS/Fedora,目前没有在Debian或者FreeBSD上测试,或许支持,或许不知道debian/FreeBSD。cd /etc/init.d mv iptables iptables.backup wget http://files.directadmin.com/services/all/iptables chmod 755 iptables*** 注意,ipables默认开启的ssh端口是22,如果你的ssh端口不是22,请手动修改iptables设置。*** 注意,ipables默认开启的ssh端口是22,如果你的ssh端口不是22,请手动修改iptables设置。启动iptables:/etc/init.d/iptables restart2) 第二步,安装block_ip.sh脚本,block_ip.sh格式可以在found here找到 .cd /usr/local/directadmin/scripts/custom wget http://files.directadmin.com/services/all/block_ip.sh wget http://files.directadmin.com/services/all/show_blocked_ips.sh wget http://files.directadmin.com/services/all/unblock_ip.sh chmod 700 block_ip.sh show_blocked_ips.sh unblock_ip.sh3)创建blocked_ips文本:touch /root/blocked_ips.txt touch /root/exempt_ips.txt去DA后台操作下Home–>Brute Forece Monitor–>IP info–>Blcok this IP.da-pojie1 da-pojie2 da-pojie34)自动封IP:vi /usr/local/directadmin/scripts/custom/brute_force_notice_ip.sh添加内容:#!/bin/sh SCRIPT=/usr/local/directadmin/scripts/custom/block_ip.sh ip=$value $SCRIPT exit $?;chmod 700 brute_force_notice_ip.sh以下是FreeBSD相关:If you’re running FreeBSD with ipfw, you’d skip steps 2 and 3, and instead, add the following code to the file:/usr/local/directadmin/scripts/custom/block_ip.sh #!/bin/sh echo “Blocking $ip with ipfw …”;ipfw add deny ip from $ip to any exit $?and don’t forget to chmod the block_ip.sh to 755.
 贝壳主机网
贝壳主机网